~~~~~~ With the Name of ALLAH ~~~~~
SQL injection is a code injection technique, used to attack data-driven applications, in which malicious SQL statements are inserted into an entry field for execution (e.g. to dump the database contents to the attacker). SQL injection must exploit a security vulnerability in an application's software, for example, when user input is either incorrectly filtered for string literal escape characters embedded in SQL statements or user input is not strongly typed and unexpectedly executed. SQL injection is mostly known as an attack vectorfor websites but can be used to attack any type of SQL database.
--------------------------------------------------------------------------------------------------------------------------------
SQL injection Types ::-
-------------------------------------------------------------------------------------------------------------------------------------------------------------
- Union Based injection( Post Injection | Get_$ injection)
- Time Base Injection
- Error Based Injection | Xpath injection
- Cookie based Injection
- Blin sql injection
------------------------------------------------------------------------------------------------------------------------
How Sql Injection works:::-
-------------------------------------------------------------------------------------------------------------------------------------------------------------
Sql injection Works only on Vulnerable Sites .
What is Meant by vulnerable::?In computer security, a vulnerability is a weakness which allows an attacker to reduce a system's information assurance. Vulnerability is the intersection of three elements: a system susceptibility or flaw, attacker access to the flaw, and attacker capability to exploit the flaw.[1] To exploit a vulnerability, an attacker must have at least one applicable tool or technique that can connect to a system weakness. In this frame, vulnerability is also known as the attack surface.
--------------------------------------------------------------------------------------------------------------------------------
How to find Vlunerable Sites ::: -------------------------------------------------------------------------------------------------------------------------------------------------------------
Finding vulnerable site is very easy with the help of Google :::
For this purpose we will use Google Dorks
here Is Some Google Dorks :::
- newsdetails,php?id= site:in
- news.php?id= site:in
- buy.php?bookid=
- bycategory.php?id=
- cardinfo.php?card=
- cart.php?action=
- cart.php?cart_id=
---------------------------------------------------------------------------------------------
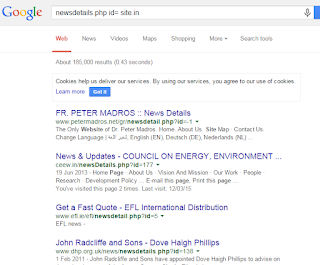
Simple Put dorks in Google it gives u lot of Vulnerable sites like that ::
------------------------------------------------------------------------------------------------------------------------
How To Know That Site is Vlunerable::::::--
---------------------------------------------------------------------------------------------------------------------
http://www.tadspec.com/index.php?id=15
this is a site now how to know that it is a vulnerable site::
for this purpose i will put A singal code ' or double coded ", or ) or \ , or # Etc Then hit enter ::
If it generates error then it means it is suitable for sql injection:::
http://www.tadspec.com/index.php?id=15'
Why Error comes::
Suppose orginal query is like that ::
Select * from world where id='15'So when we put ' Query becomes like that ::
Select * from world where id='15''Due to Dismatch SQL Generates a Error Messages which is very Good for attackers:::
SQl is very Friendly Language. I hope You Understand That Point ::
Types of Error ::::
-------------------------------------------------------------------------------------------------------------------
- Warning: main(languages//headlines.php): failed to open stream: No such file or directory in /var/www/html/includes/connect_site.php on line 50
- You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ''1'''
- Content Missing Error ( Page normally loads with something missing)
--------------------------------------------------------------------------------------------------------------------
In NexT tutorial We will Discuss on How to find number of columns ,Vulnerable Columns and We will Discuss on Nature of errors ...Means which error how To solve ...
(Author::: Afghani:::)
at line 1

0 comments:
Post a Comment